Hyundai Polytech recognizes information security as an essential element for sustainable management and has established and faithfully practices an 'Information Security Policy' as follows to safely protect Hyundai Polytech's assets from information security threats.
1. Establish information security organization and system suitable for the company's scale and business, and continuously improve information security levels.
2. Establish and continuously develop prevention, detection, and response systems for information security incidents to create a safe business environment.
3. Improve information security awareness of company employees and partners to establish an information security culture.
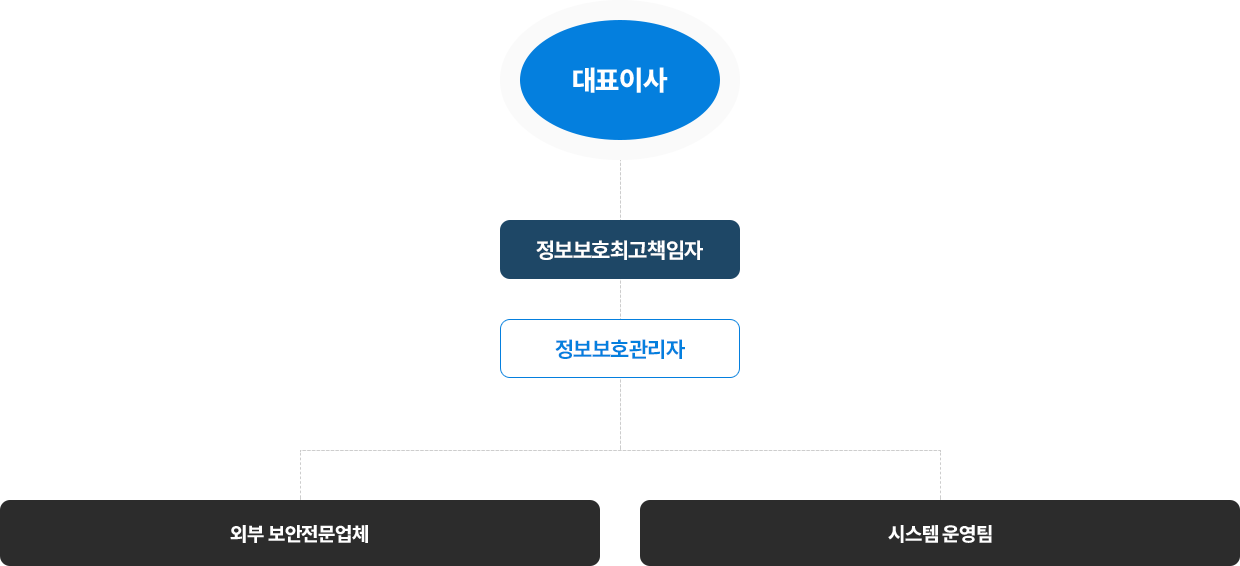
Hyundai Polytech is building an information protection organization to safely protect against information security threats.